e-Health and m-Health app development has undergone rapid growth. Nowadays, there is a trove of healthcare applications on the market. But, how secure are they? Can users pin their faith on them? Unfortunately, cannot, which has been proved by recent research and studies. While healthcare facilities actively take medical service delivery to digital channels, their applications do not keep up with common security standards. So, as long as healthcare app security has become a hot topic, let’s consider it in detail.
The Most Common Security Vulnerabilities in Healthcare Apps
In the realm of healthcare app security, we can differentiate the main vulnerabilities to be taken into consideration:
An application may communicate with an insecure backend web endpoint leading to insecure API functioning.
Unauthorized parties can access sensitive data if incorrect encoding or file permissions are used for data storage.
Insecure client-server connection
If proper cryptographic protocols are not used, communication between a healthcare app and a server may be insecure, and it may serve as a loophole for cybercriminals if they leverage the same WI-FI connection.
A healthcare application may leak private data available to other installed applications or to cybercriminals who have immediate access to a gadget.
Improper user authentication
An app may have an improper authorization that can be easily bypassed. Therefore, unauthorized parties can get access to private data in order to use it for their own benefit.
If improper encryption algorithms have been utilized, it can result in poor protection of patients' confidential data.
A healthcare app may not properly “sanitize” data inputs before their execution, which makes the data fragile.
Insecure session handling
As a rule, applications store cookies on users' devices till a session is active. If it is done insecurely, cybercriminals can take complete control of the session.
Due to the poor binary protection, cybercriminals can reverse the mobile app binary getting access to a source code, algorithms, and important values of an m-Health app. It is indeed a critical vulnerability that must be thoroughly checked.
Why are healthcare apps so vulnerable?
For several years running numerous studies have shown that the healthcare industry is one of the core targets for cybercriminals in the whole world. PHI that is protected health information costs a lot of money on the black market. Therefore, for cybercriminals, the healthcare applications are the goose that lays the golden eggs. Data leakage discovery and reporting take some time that is enough to sell stolen records online before weak spots in the app security are identified and patched. Besides, apart from patient records, healthcare provider networks can also contain valuable financial information.
Taking all this into account, hackers do their best to find any loopholes in healthcare applications and get access to sensitive information.
So, it is crucial to make sure that your healthcare app is securely protected against possible data leakage and cyber attacks. Besides, it is even more important to have your finger on a pulse and frequently update your healthcare app. It is crucial because as time goes by, technologies get obsolete and hackers figure out more and more ways to get access to the app data if it is not securely protected.
2020 Security Report on Global m-Health App Threats by Intertrust
Since the security of modern healthcare applications gives cause for concern, security experts of Intertrust decided to conduct their own research in order to reveal the actual state of affairs.
Intertrust is a globally recognized technology and licensing company with years of research and development in computer security and digital trust. The company is based in Silicon Valley but has regional offices across the whole world.
The team of Intertrust experts studied one hundred m-Health applications of various types using diverse techniques and being guided by the globally recognized security standards.
According to 2020 Security Report on Global m-Health App Threats by Intertrust:
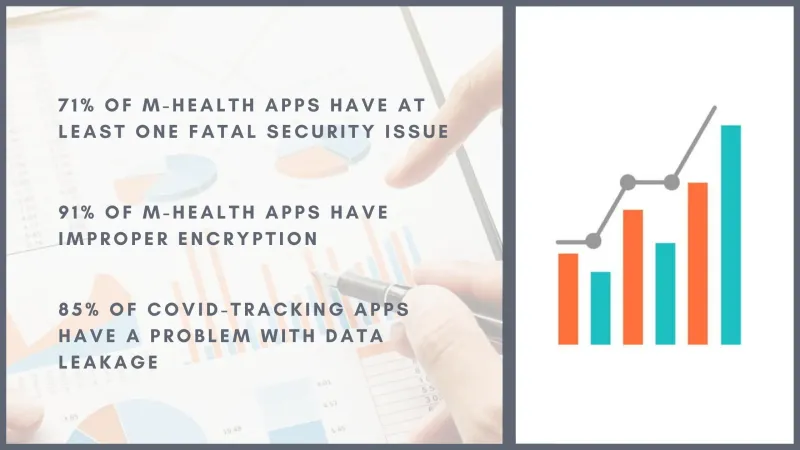
71% of m-Health applications that have undergone testing contain as a minimum one fatal security issue;
91% of tested mobile healthcare applications have improper encryption;
Data leakage is the main security problem for about 85% of COVID-tracking applications;
Most m-Health applications have numerous security problems related to data storage.
The experts of Intertrust thoroughly analyzed detected threats and came to the conclusion that 83% of crucial security vulnerabilities of m-Health apps could have been eliminated or at least mitigated by means of code obfuscation, tampering detection, and cryptography.
Importance of security testing for healthcare apps
Software testing plays an important role in the development of any software. When it comes to healthcare apps, comprehensive testing is a compulsory activity. Plenty of diverse tests must be conducted to ensure that an app works properly and meets all technical requirements. Particular attention should be paid to security testing checking that patients' private data is securely protected and the app can withstand the most various cyber attacks. Complete security testing is made up of penetration testing, vulnerability scanning, security scanning, posture assessment, risk assessment. etc.
The main advantages of healthcare app security testing:
Secure PHI protection is a precondition for HIPAA compliance. Security testing detects vulnerabilities and possible risks as well as confirms that PHI is not visible in URLs, caching is properly maintained, encryption protocols are properly used, access control is tokenized and gated, etc.
Security testing validates that the leveraged data storage techniques are effective and reliable. For this reason, applied security solutions, encryption algorithms, and data management are thoroughly studied and checked during security testing.
Security technique validation
During security testing, experts assess the efficiency of the leveraged security techniques and mechanisms, including 2FA or MFA and encryption algorithms.
As a rule, healthcare apps imply active data exchange. One of the major goals of security testing is to check whether data is appropriately encrypted to avoid unlawful data trespassing during its transmission.
Poor IAM, which is an abbreviated form of Identity and Access Management, can serve as a loophole for cybercriminals. That is why to ensure proper app access approval or deny, security testing assesses how well access levels are differentiated and managed.
Security testing also suggests an in-depth analysis of possible security risks. Detected risks are usually prioritized as Low, Medium, and High, and corresponding measures are recommended to mitigate them and improve app security.
HIPAA compliance is obligatory for healthcare apps, and proper security testing is a great way to attain it. A HIPAA-compliant app is synonymous with confidence and trust. As a result, potential users make a decision to utilize it, and investors consider investing in it. Thus, security testing helps build trust, which in its turn boosts business growth.
How to provide the proper healthcare app security?
Solid security is an essential characteristic of an awesome and successful healthcare application. That is why such applications must be created with security in mind. Below you can see some practices considered to be extremely helpful in terms of app security:
Encryption is one of the most powerful methods to securely protect confidential data. Encryption is a fire-sure way to defend all communication channels, DBs, server files, messages, and so on.
Encryption implies the use of algorithms that make usual text unreadable transforming it into ciphertext. For decryption, it is needed to utilize a special encryption key available only to corresponding medical staff and patients.
Besides, it is advised to use cryptographic protocols like Transport Layer Security or Secure Socket Layer that provide secure and private client-server communication.
Proper user authentication
The easiest way to protect a healthcare application from unauthorized access is by implementing multi-factor authentication (MFA) that provides access only if a user has confirmed in various ways that he or she is indeed entitled to gain access to confidential data. MFA is especially helpful in case of device loss or theft, protecting the owner’s confidential data from unauthorized access.
Two-factor authentication is one more viable option to make sure that just legitimate users are allowed to access the app. When 2FA is utilized, app users must confirm identity by means of a password entry and one of the secondary components, for instance, biometrics data or a security code submitted via SMS.
Ensure data accessibility
It is deemed to be a good practice to back up critical information or provide multi-location data storage to ensure data accessibility in case of data theft.
Complete healthcare app testing
As we have already mentioned, comprehensive software testing, and especially security testing, is compulsory for healthcare applications. To feel confident that your corporate data, as well as your patients’ confidential information, is securely protected, it is essential to check whether the app can withstand possible hacker attacks and scan it for possible vulnerabilities. A team of professional QA specialists with rich expertise in security testing can conduct all the required tests, assess the security level of AUT, and provide some useful recommendations.
Compliance with regulations
As a rule, healthcare applications must match the state norms and regulations that define data protection standards. For example, healthcare apps designed for the US market must meet the norms of HIPAA, apps for the EU market must correspond with GDPR, while healthcare apps targeting the Canadian market must correspond with PIPEDA. So it makes sense to study corresponding regulations to ensure app compliance with them as well as required security standards.
Conclusion
To mitigate the risk of sensitive data theft and provide secure patient data protection, a wide array of practices is recommended, and some security standards are considered to be compulsory. Still, some providers are so eager to launch a healthcare app as soon as possible that they hardly pay any attention to privacy and security issues. According to numerous surveys conducted by the most reputable companies, most healthcare providers fail to ensure the proper security of their apps. As a result, not only their patients’ private data is in danger, but also their own healthcare business.
To provide patients with valuable healthcare applications and retain them it is vital to ensure data security. So, developing your e-Health or m-Health applications you should use the most effective security techniques, conduct comprehensive testing, and ensure compliance with state regulations.